Potential design patterns for open APIs in the utilities sector
The prototyping for this report uncovered several potential design patterns for solving different problems, from authentication to giving consent to controlling access and transparency. Many of these could be useful for designing services for open APIs in the wider utilities sector.
- Select what data a service can share
- Authorise using a letter
- Authorise using another factor
- Combine open, shared and closed data
- Consent by SIM card
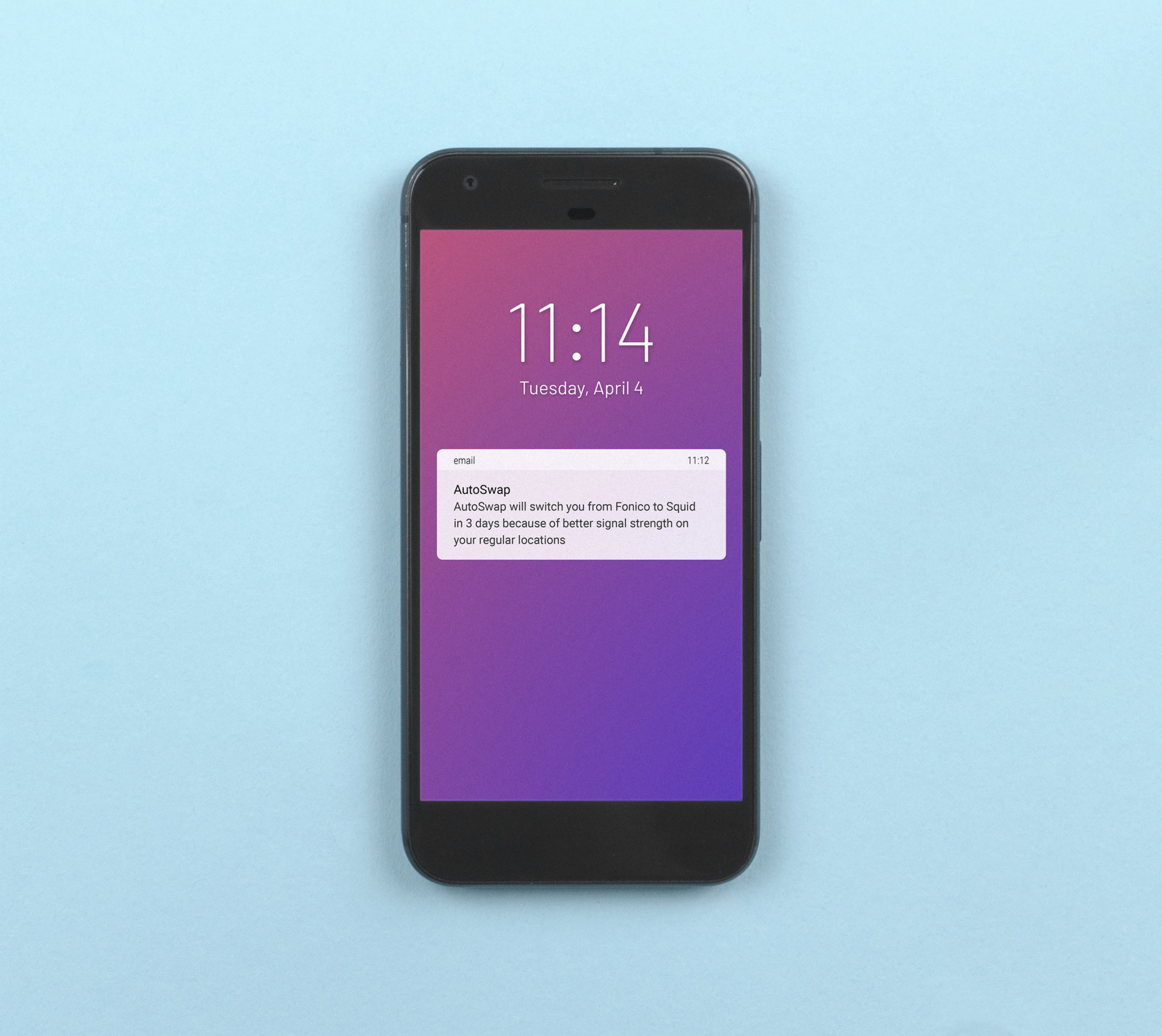
- Automated switching
- Future switch notice
- Account history across providers
- Display multiple utilities
- Add another person to an account
- Get group consent
- Hand over accounts to new people
- Public space notices
- Human-readable data request
- Machine-readable data request
- Minimise data collection
- Plenty of time to opt-out
- Opt out by text
- Opt out by WiFi proximity
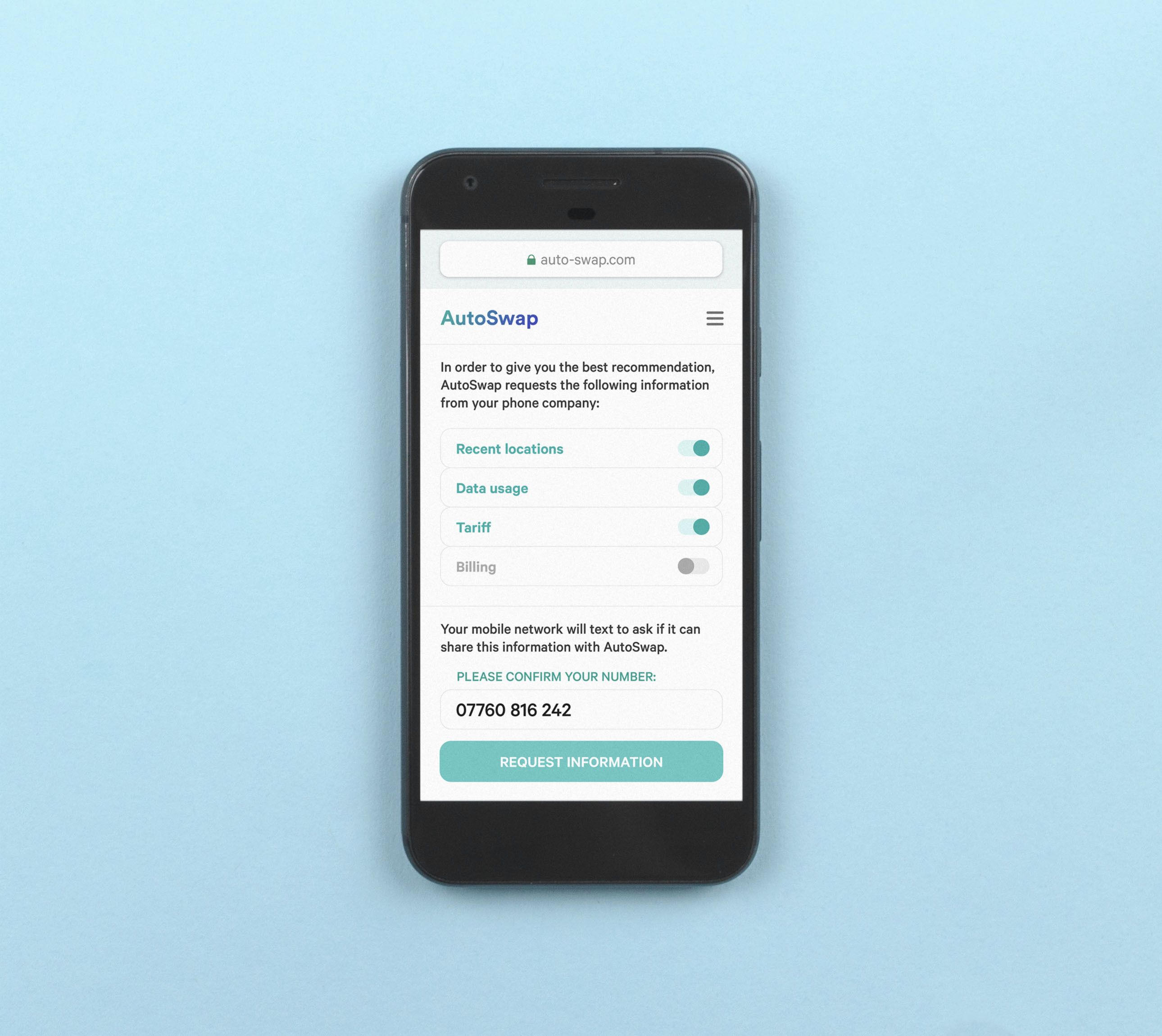
Select what data a service can share
Deciding what types of data one service is allowed to request from another using an open API. This gives people control over what data they reveal to an organisation.
Authorise using a letter
Letters with printed codes to access data from telecoms and other utilities. Using a letter connects the recipient to a physical address. Codes can be used in conjunction with other information and can be limited to single-use to reduce the risk of fraudulent access.

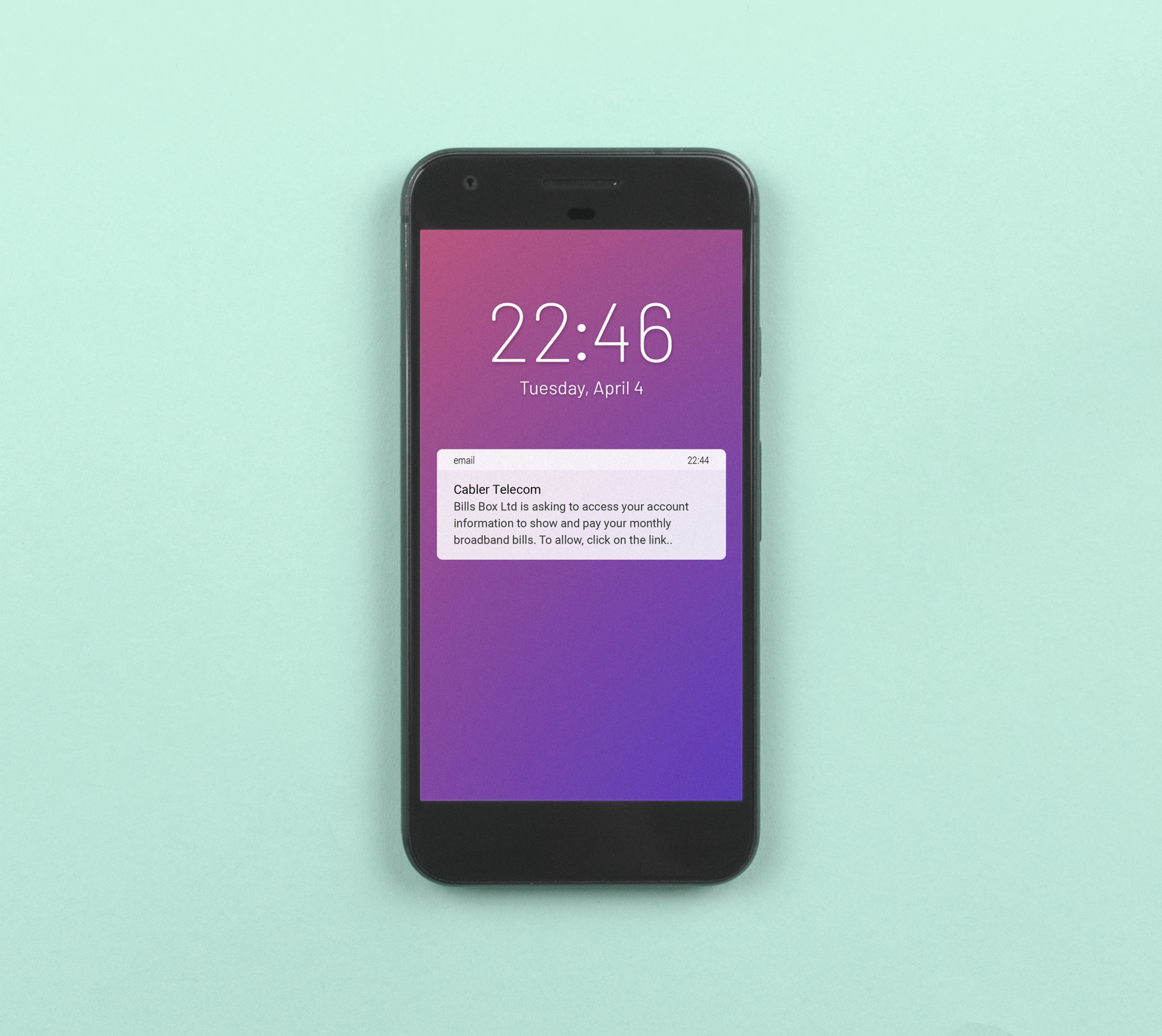
Authorise using another factor
Emails or text messages are used as extra authentication when data is requested from open APIs. This restricts access to whoever controls a known email address or phone number.
Combine open, shared and closed data
Making more informed decisions by combining data about networks and people.
Consent by SIM card
Putting a virtual SIM card into a phone gives it the ability to freely switch between networks. Physically putting this small microchip into a device creates a moment of consent, which grants the phone permission to work on a number of networks.
There are parallels with electricity meters in the home, which are considered as infrastructure rather than being tied to a particular supplier.

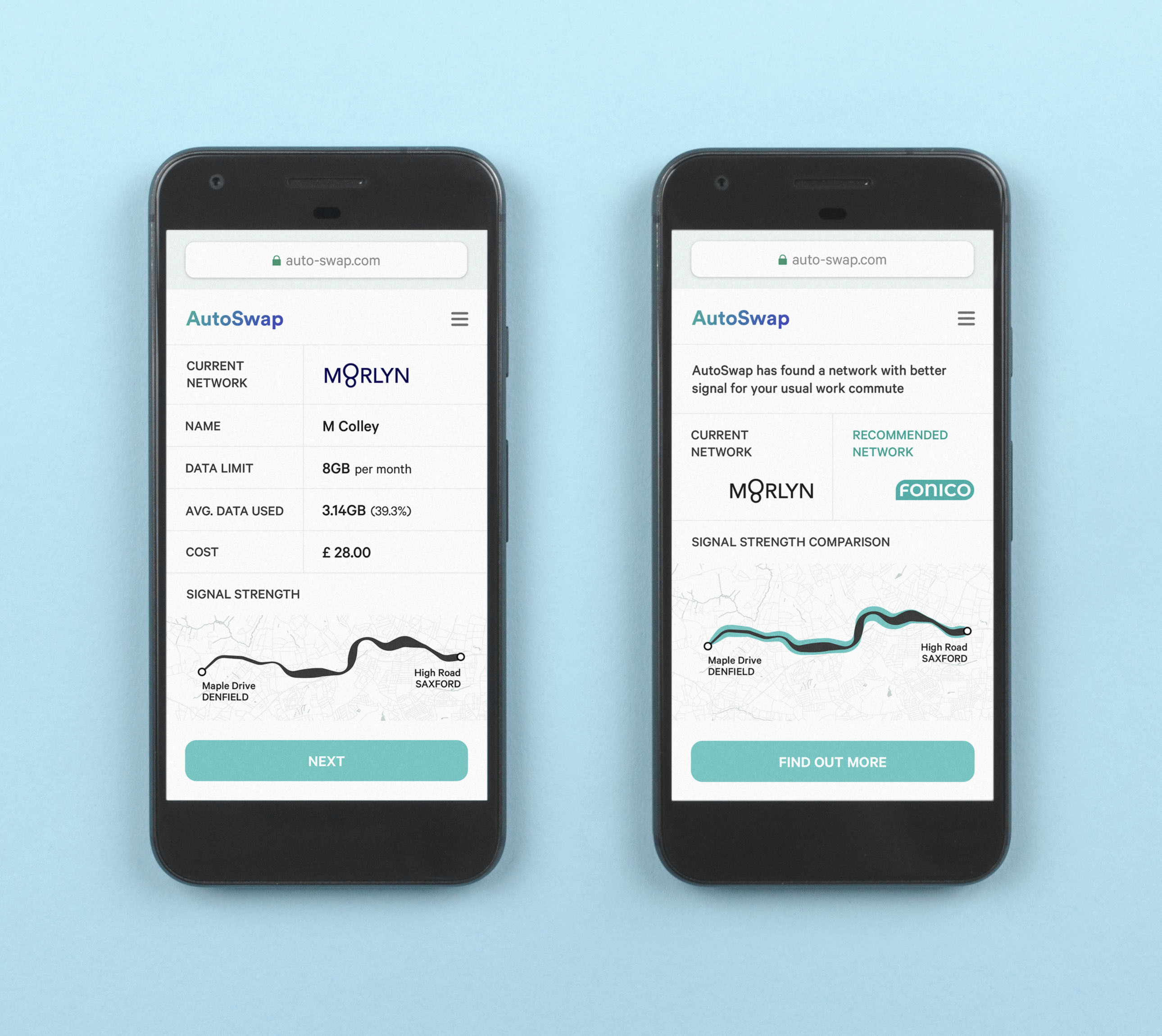
Automated switching
Delegated authority allows a service to automatically find and switch service providers. The first step is setting preferences to seed recommendations — initially there is no automation.
Over time, as trust increases, more autonomy might be acceptable, leading to automatic switches without explicit permission each time.
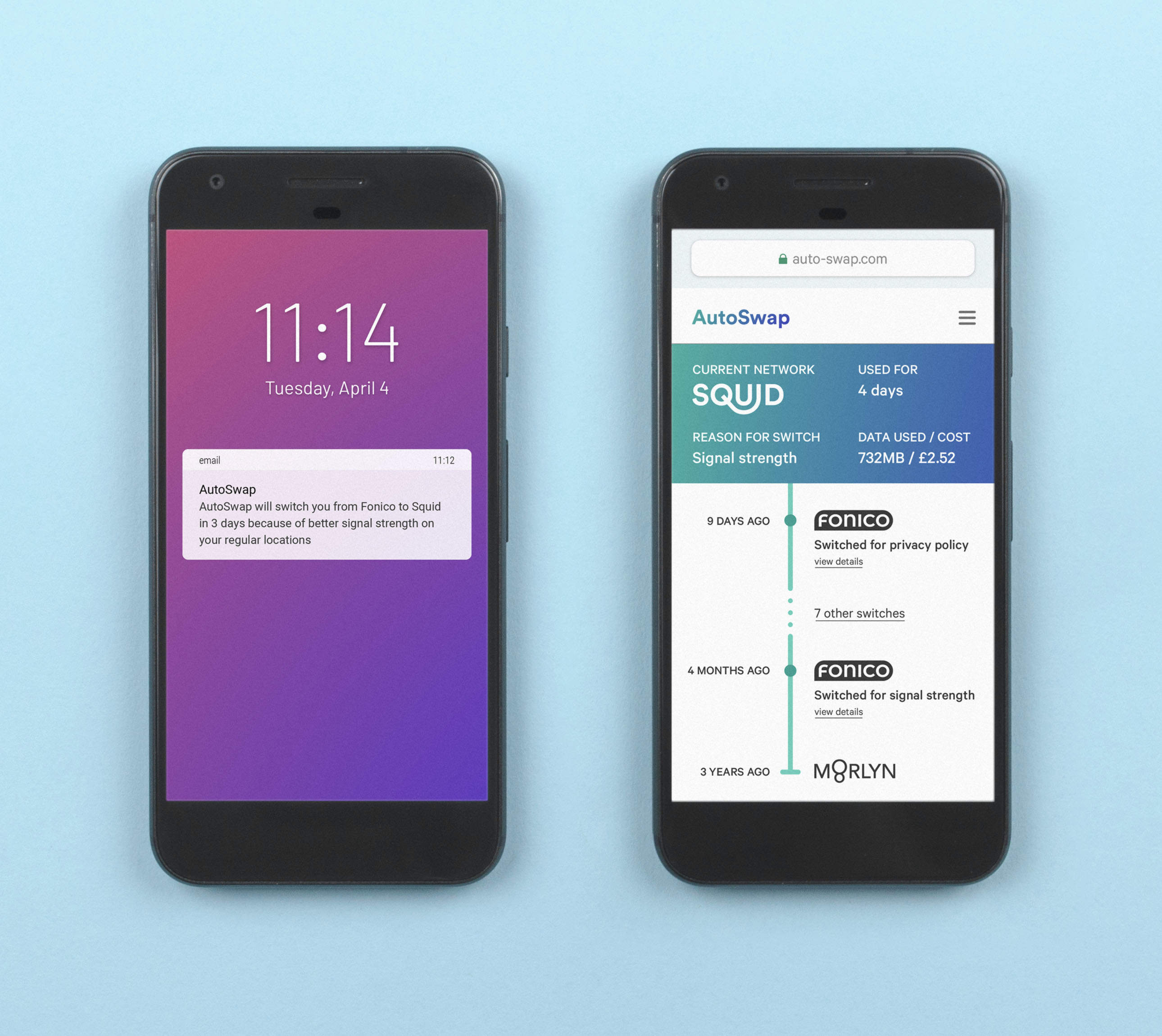
Future switch notice
An automated action, like switching phone company, includes plenty of notice to allow the person to review or cancel the action.
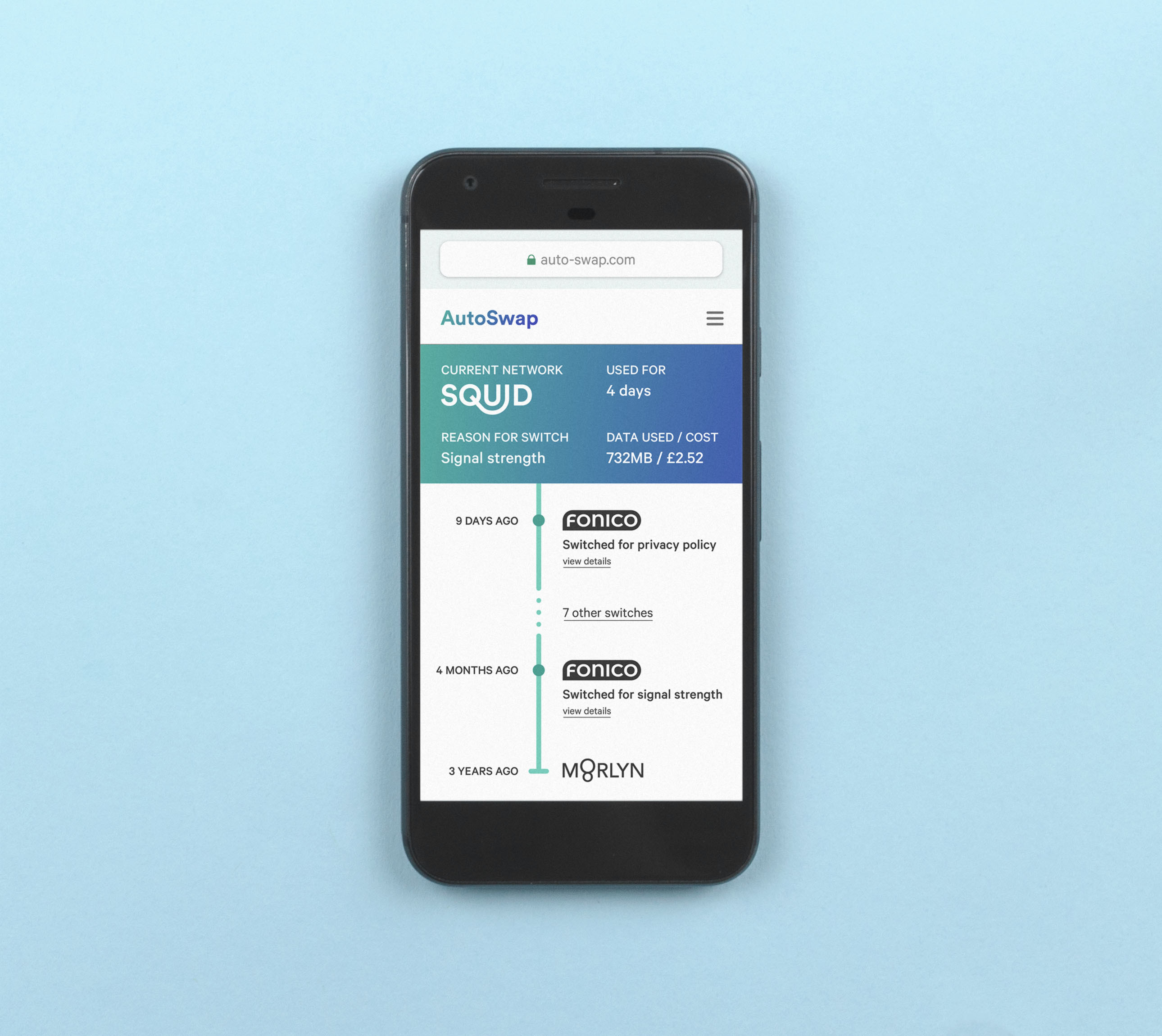
Account history across providers
A visible history of data usage, access and spending for one person from a series of historical accounts.
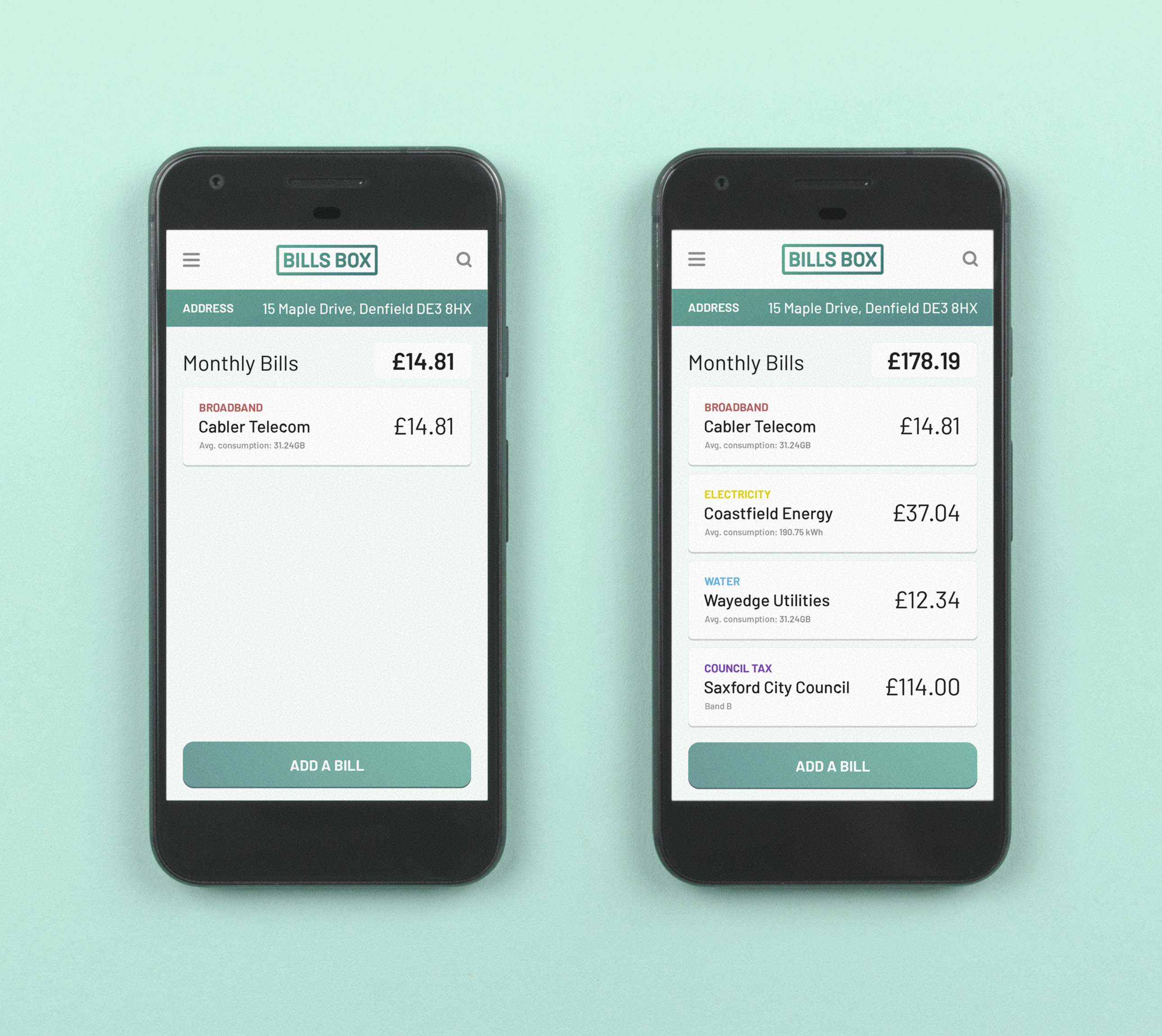
Display multiple utilities
Multiple utilities can be made visible and manageable from one service.
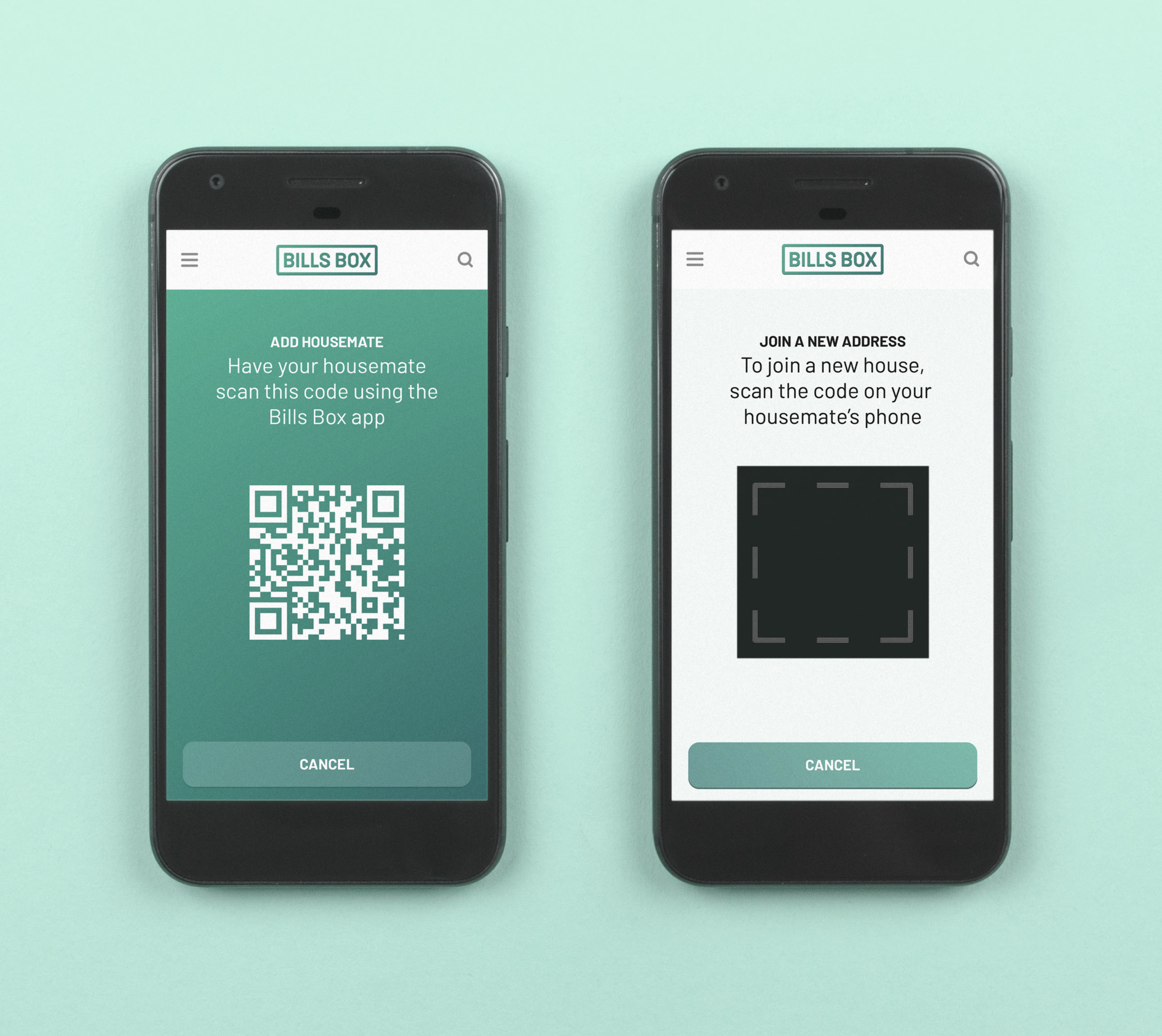
Add another person to an account
Codes generated allow people to share the rights and responsibilities for a bill and shared data.
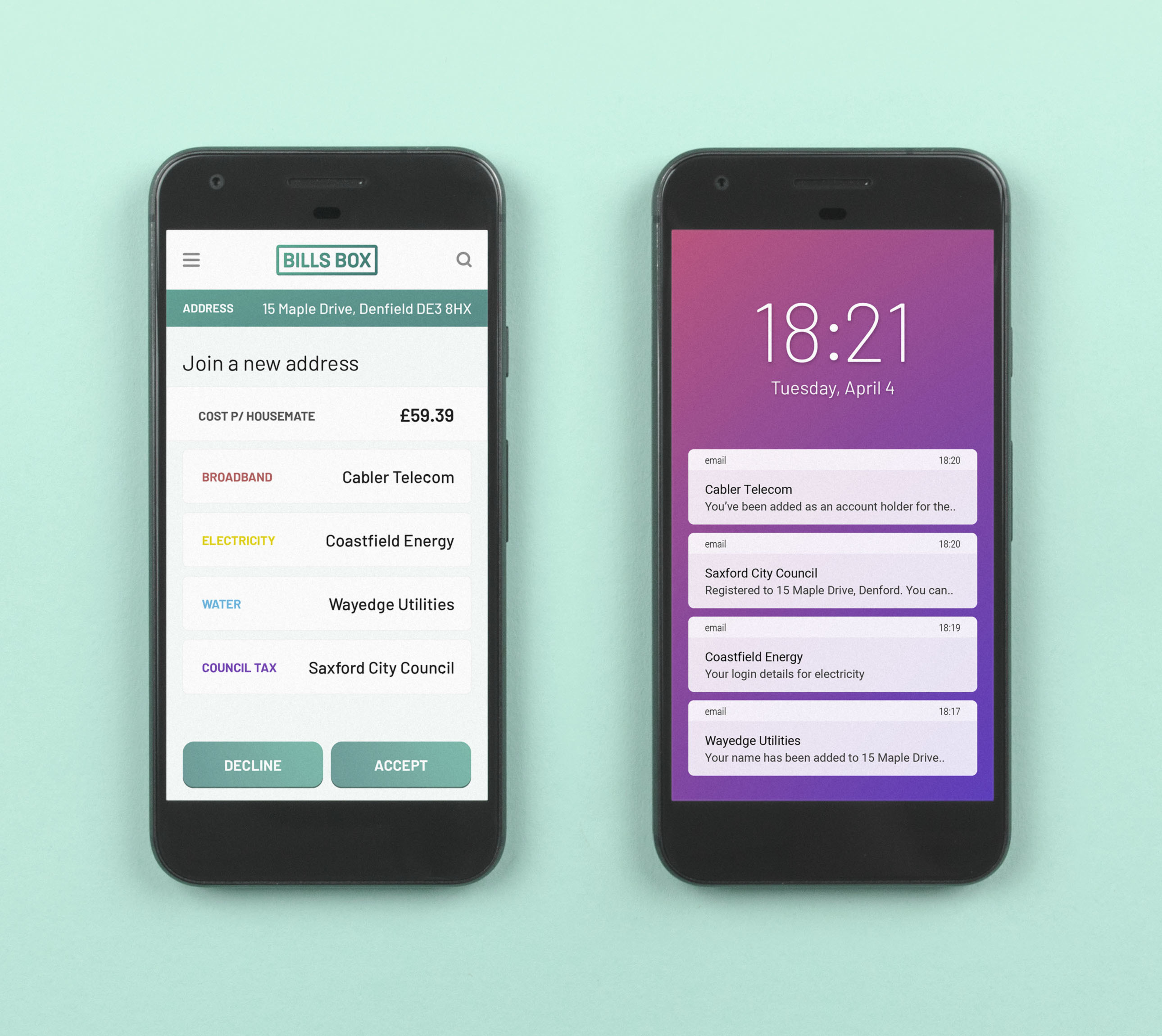
Get group consent
Collect consent for group decisions for actions which affect multiple account holders, for example people moving out of a shared home.
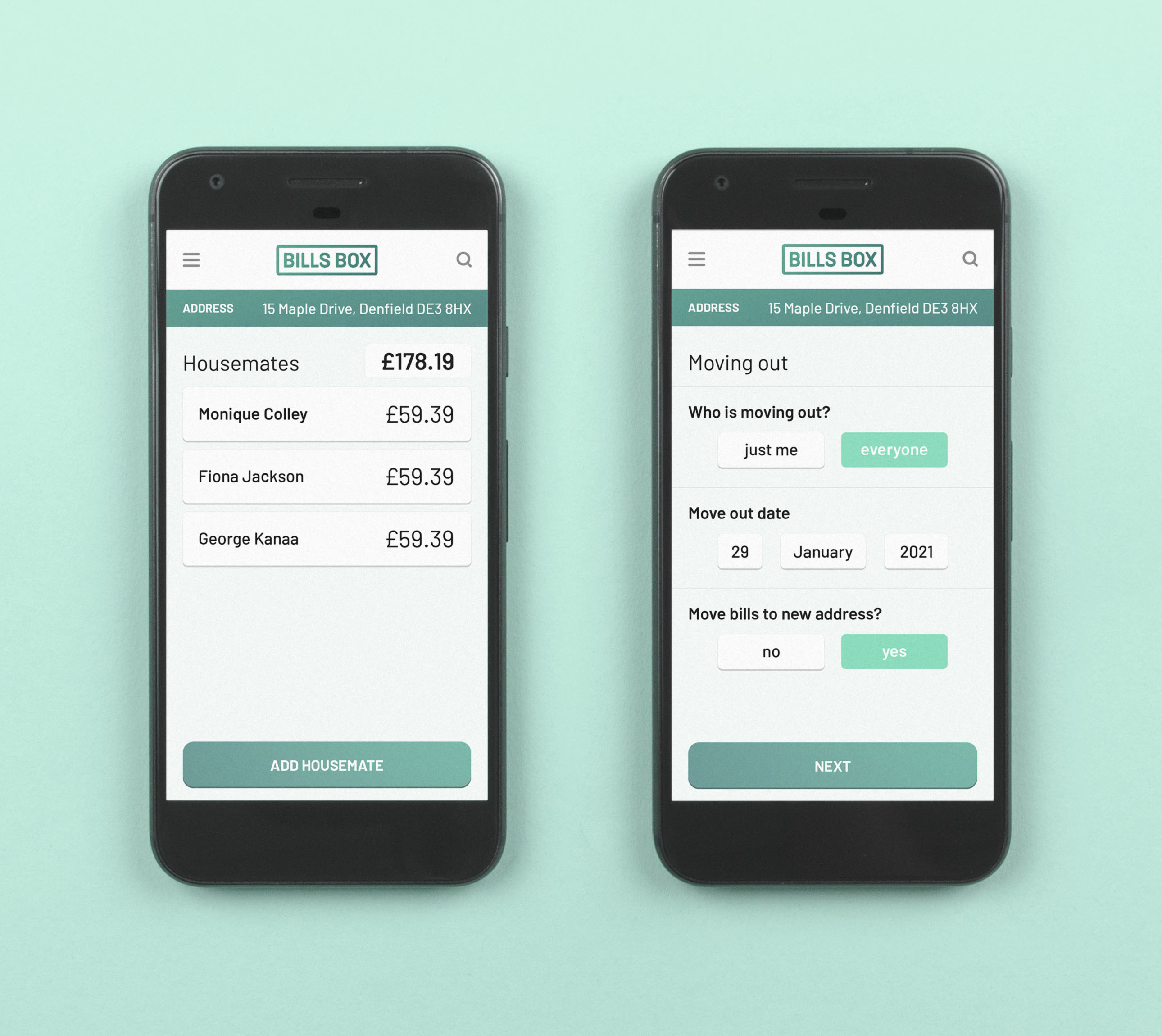
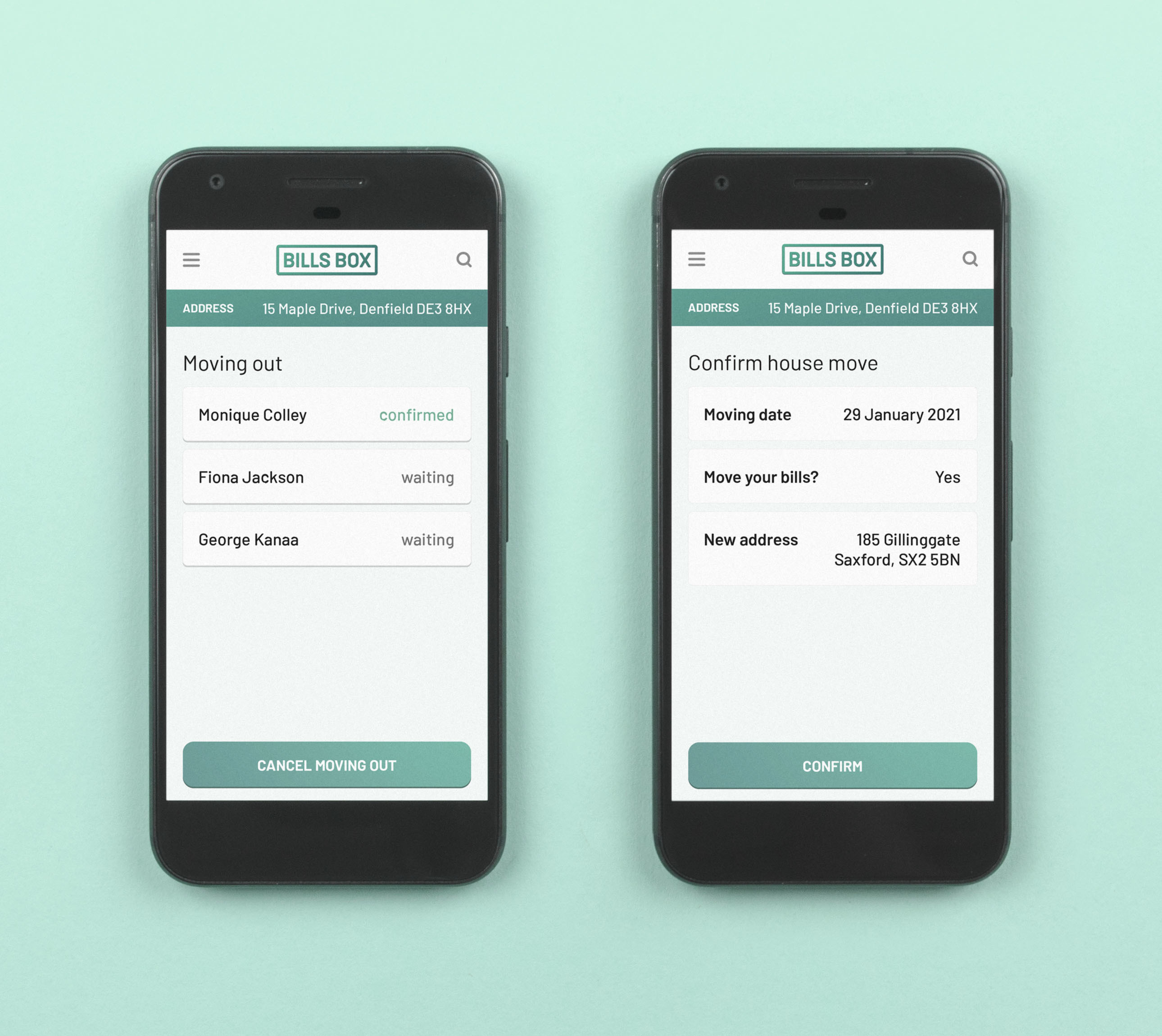
Hand over accounts to new people
Allow people to take over rights and responsibility for bills.

Public space notices
Communicate when certain data about a person is collected as they enter a space. This includes the reason for data collection, what data is collected and how to opt out.

Human-readable data request
Explain potential data collection in plain, accessible language.
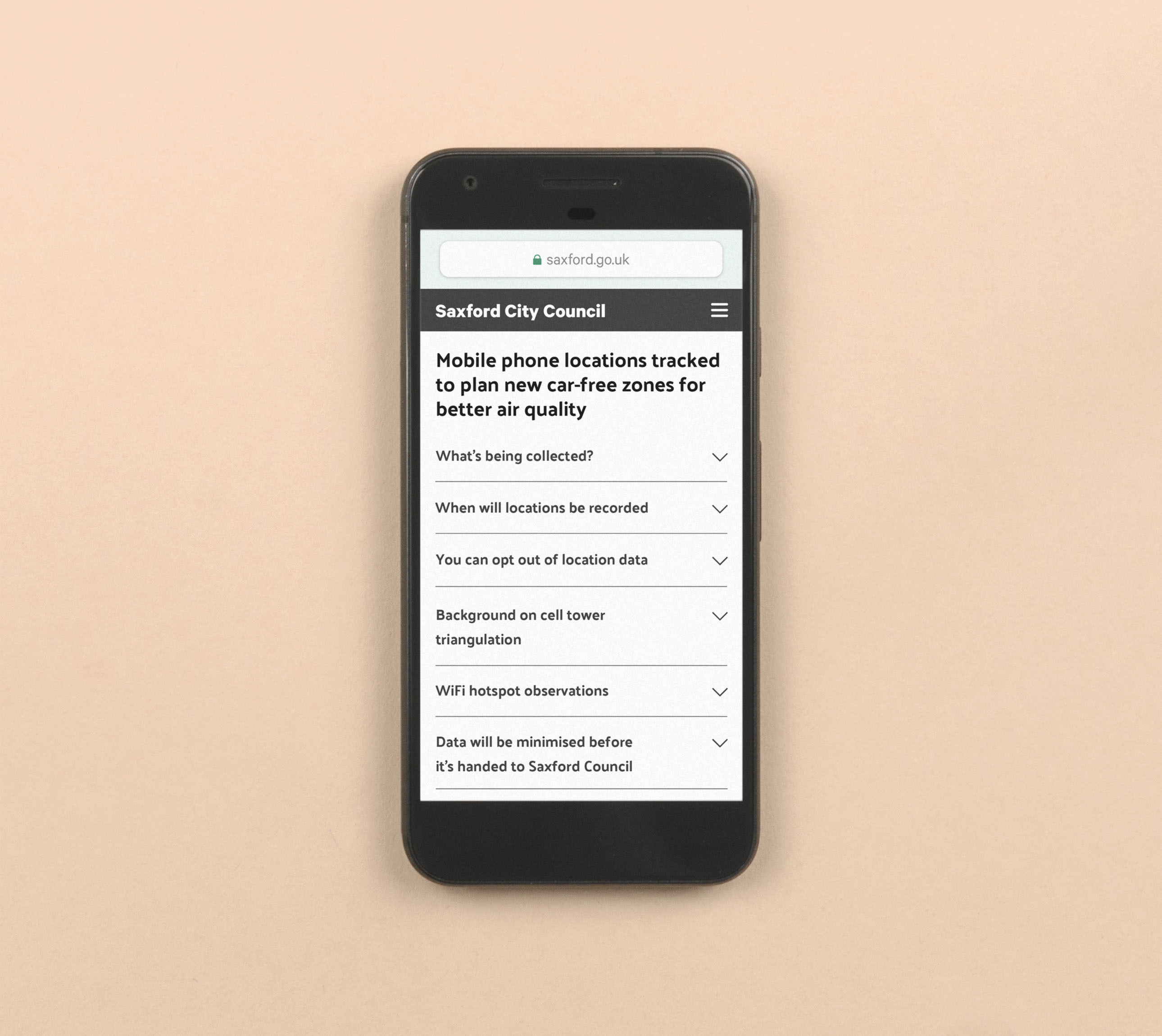
Machine-readable data request
Place a data request in a format a computer can easily access and analyse.
Data requests could be submitted to regulators, posted to public notices and submitted to telecoms companies in exactly the same format, ensuring traceability of a particular request.
Minimise data collection
Limit bulk data collection to certain times, location accuracy and other restrictions, to ensure data doesn't contain personally identifiable information.
Plenty of time to opt-out
Before data collection happens, people are given ample time to find out more and decide whether to opt out or not.
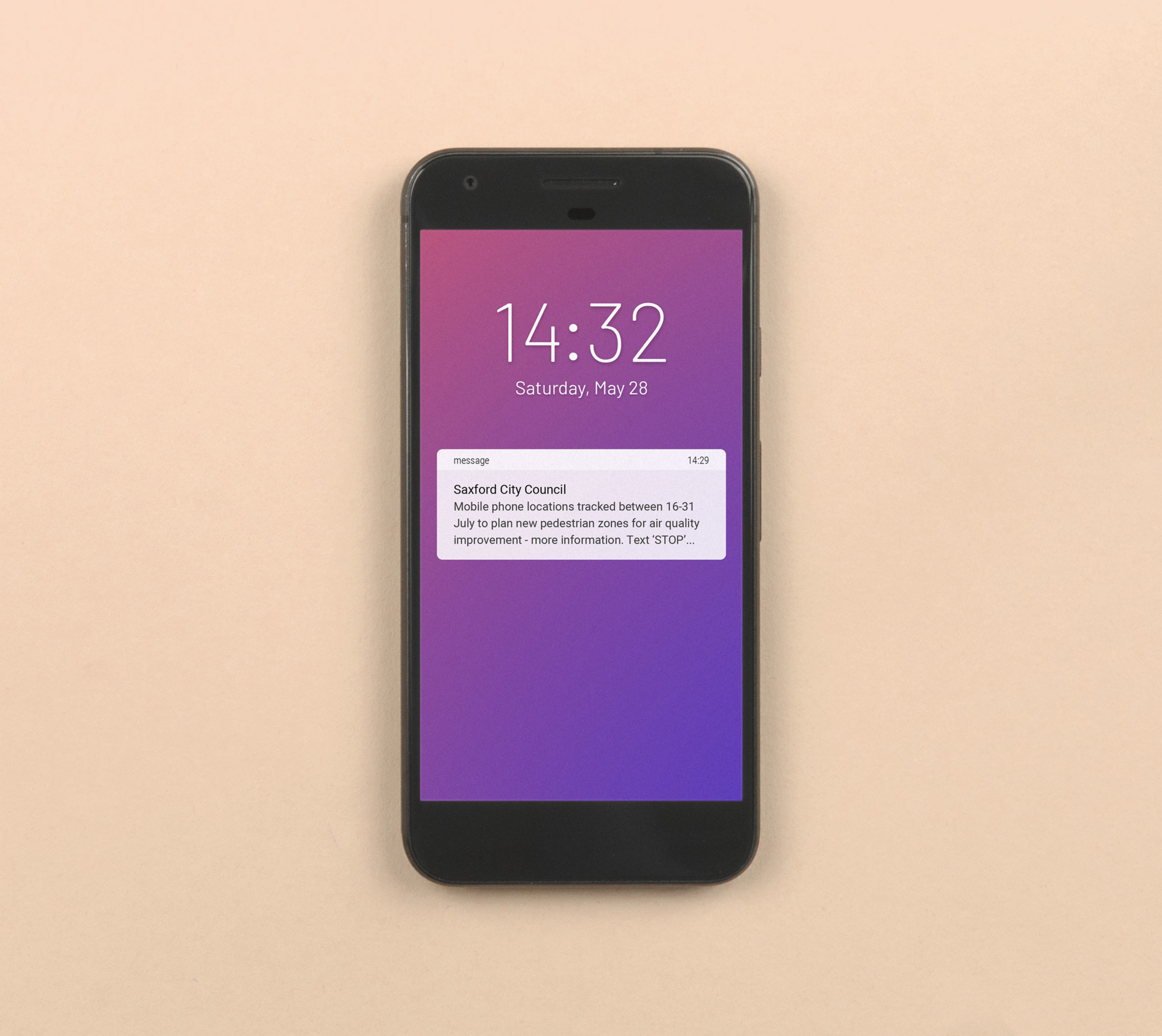
Opt out by text
Text messages inform people of data collection and let them reply to opt out. Text messages can be sent to people in specific locations using a system such as Cell Broadcast.
Opt out by WiFi proximity
Hold a phone close to a WiFi hotspot to stop it collecting data about you. The hotspot detects the device is close by the latency and radio strength.

 Open APIs in the Telecoms IndustryContents
Open APIs in the Telecoms IndustryContents